The IP Protocol
Recall earlier: the TCP (transport layer) protocol is implemented
in the two end systems involved in communications.
TCP relies on the Internet Protocol to deliver
packets of data from one end system to another. The packets which
IP delivers are usually called datagrams.
Datagrams navigate zero or more (sometimes many) routers,
interconnecting
the individual networks which together make up the Internet.
The word "Internet" is just a contraction of the phrase
"Interconnected Networks".
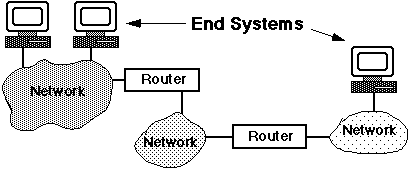
A router is essentially a special-purpose computer whose sole
function is to transfer datagrams between networks. In earlier
times, they were called "IP Gateways". The general structure of
the Internet can thus be envisaged:
IP Addressing
The concept of a global Internet addressing scheme is
fundamental to IP.
Every Internet-connected system has a unique Internet host
address. This is a 32
bit, or 4 byte, binary number.
Internet addresses are written as a dotted sequence of the form:
aa.bb.cc.dd
where aa, bb, etc, are the decimal values (ranging from 0
to 255) of
the 4 bytes which make up the internet address, for example:
149.144.21.60
This is called the "Common Internet Address Notation".
Internet addresses are commonly referred to as "IP addresses".
149.144.21.60 is the IP address of "ironbark", or to use its full
name, ironbark.bendigo.latrobe.edu.au.
We shall see later how the name of a computer (ironbark,
redgum, bindi, etc) is mapped to its IP address.
Note that the traditional Internet literature refers to
internet-connected computers as hosts, which reflects
the historical nature of computers as multi-user timeshared systems.
"Two Part" Addresses
The 4 byte internet address consists of 2 parts, the network part
and the host
part.
- The network part must be the same for all hosts connected to
the same network.
- The host part must be unique within each specific network. It
is used to deliver the datagram once it has been routed to the
appropriate network.
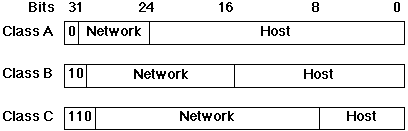
The structure of an IP address differs depending on the class of
the local network to which the host is connected:
- Class A Network
- the first (or leftmost) field, or byte, of
the address specifies the network number and class, and can
take values from 1 to 126.
- Class B network
- the leftmost two fields (bytes) specify the
network number and class. The first field is in the range from
128 to 191, and the second from 1 to 254.
- Class C network
- the leftmost three fields specify network
number and class.
The first field can be from 192 to 223, the second from 0 to 255,
and the third from 1 to 254.
IP Address Classes
The Internet address format can be described graphically:
- Eg 1:
- in a class A network, only values from
00000000 to
01111111 are
possible. Of these 128 combinations, 126 are permitted (networks 0
and 127 are reserved for other purposes). Hence there can only
ever be 126 class A networks, each of which can have a huge
number of hosts.
- Eg 2:
- ironbark's IP address is
149.144.21.60 This is a class
B network (149.144), and ironbark's host ID is 21.60
- Eg 3:
203.17.3.5 is a class C address. The network number is
203.17.3, and the host number is 5.
Network numbers above 223 are also reserved for special purposes,
outside the scope of this subject.
IP Address Miscellany
The broadcast address is the address used to send a
datagram to all hosts on the
local network simultaneously. This is the address given by the
network number
followed by all binary 1's in the host part of the address.
For example: A broadcast address for a host on an example Class-C
network is:
195.96.97.255
Where Class-B networks (and, nowadays, class C also) are in use,
the host part of the address is commonly split, for management
purposes, to allow
subnetting -
typically this involves defining 254 subnets each of 254
hosts. Each of these
subnets behaves, for all intents, like an independent class-C
network: thus:
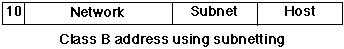
Exactly which bits of the subnetted address are used for the
network/subnet part and the host part is defined using an address
mask, or netmask thus:
255.255.255.0
IP Datagrams
IP transmits data in packets called datagrams. A datagram
contains a
header and some data, thus:
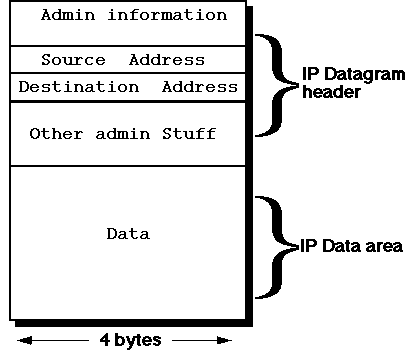
Notes:
- The total length of a datagram can be up to 64 KB, but is usually
less than 1500 bytes
- The header contains the source and destination IP addresses as
well as various other administrative data, a minimum of 20 bytes in
total
IP: Connectionless Datagram Delivery
IP data transfer across an internet is based on three fundamental
principles:
- Unreliable delivery
- delivery of data is not guaranteed. A
packet
of data may be lost in the network, may be duplicated (ie: delivered
twice) or may be delivered out of order. The IP service will not
detect such conditions, nor will it notify the sender or receiver if
they occur.
- Connectionless delivery
- each packet is treated entirely
indpendently of all others. No information is kept as to which
packets have been forwarded, and packets may travel over different
routes to the same destination.
- Best-Effort delivery
- the packet delivery mechanism is
engineered to
always deliver packets if possible. It will not gratuitously drop
packets: unreliability should only occur when underlying resources
(eg buffer space) are exhausted.
These specifications allow the IP service to concentrate on its job:
delivering packets. As we have seen, higher level protocols
(usually TCP) transform the IP service into a reliable, sequenced
interprocess communications mechanism.
IP Routing
There are two levels of complexity involved in IP routing:
- Local delivery
- when the IP software is presented with a
datagram
for delivery, it first checks the network part of the destination
address to see if matches its own network number. If it does, then
the datagram can be delivered locally, and is simply handed to the
physical network delivery system (typically an Ethernet device
driver) for direct encapsulation and delivery.
- Internet delivery
- if the network numbers are different, then
the
datagram must be forwarded to a router (or IP gateway). In this
case, the datagram is forwarded (using direct delivery as above) to
the appropriate router for on-delivery
- Datagrams cross gateways (routers) from network to network until
they reach a network where they can be locally delivered.
- The IP software must keep a routing table to know the
IP address of
an appropriate router. This is commonly done by defining a
default
route for each network machine.
- Note that routers must have (at least) two IP addresses!
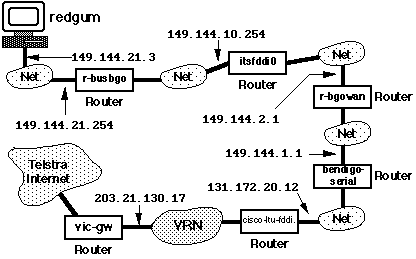
The Structure of the Internet
The Internet consists of networks (or, more commonly nowadays -
subnets) connected by routers. The traceroute operation shows
the path a datagram takes - the following traceroute
is from redgum to the Victorian Regional Network (VRN).
1 r-busbgo (149.144.21.254) 1 ms 1 ms 1 ms
2 itsfddi0 (149.144.10.254) 2 ms 2 ms 2 ms
3 r-bgowan (149.144.2.1) 4 ms 2 ms 3 ms
4 bendigo-serial (149.144.1.1) 214 ms 108 ms 84 ms
5 cisco-ltu-fddi.latrobe.edu.au (131.172.20.12) 37 ms 56 ms 60 ms
6 vic-gw.vrn.EDU.AU (203.21.130.17) 140 ms 143 ms 90 ms
The Transport Layer Revisited: UDP
The User Datagram Protocol provides a connectionless alternative
transport service to TCP for applications where reliable stream
service is not needed. UDP datagrams can be droppped, duplicated or
delivered out of order, exactly as for IP.
The UDP transport service add to IP the ability to deliver a datagram
to a specified destination process using a port abstraction,
in an
analogous way to that used by TCP.
Examples of applications where UDP is used include:
- Any application where loss of a datagram is not critical because
later datagrams will imply the missing information. Examples
include:
- A "timekeeper" host sends the current "wallclock" time to a slave
host.
- Routers broadcast copies of their routing tables every 30 seconds.
- An application process which performs its own error correction is
used.
- The reduced overhead of connectionless operation suits some
time-critical applications where (occasional) loss of data may be
unimportant. An example is voice communications over the Internet.
This lecture is also available in PostScript format.
The tutorial for this lecture is
Tutorial #07.
[Previous Lecture]
[Lecture Index]
[Next Lecture]
Phil Scott





