EDI - Electronic Data Interchange
Of all the business applications of computer networks,
this is
proving to be the single most important.
What is EDI?
- EDI is direct computer-to-computer[1]
exchange of data normally
(or previously) provided on standard business paper documents.
- Can be implemented within a business, but normally used
between companies for the following reasons:
- Cost savings due to elimination of re-keying, printing,
courier costs
- Speed: communications can be essentially instantaneous
- Reduction of errors
- Security
- Integration with other office automation applications
- Just-in-time deliveries.
- Use of EDI is now regarded as essential in many large
manufacturing companies, and its use will soon extend to smaller
companies.
[1] More correctly, of course, we should say
"application to application" data transfer
EDI Standards
The basic concept of EDI is that companies agree to a
standardised
format of EDI messages which are then unambiguously exchanged
using a reliable, connection-oriented computer network delivery
service.
There have been two proposed EDI standards:
- ANSI X.12
- developed in the US and widely adopted, although
not
an international standard[2]. Will eventually
(post-1995?) be
replaced by:
- EDIFACT
- (EDI For Administration, Commerce and Transport),
originally developed by the U.N. (?) and submitted to ISO for
ratification as an international (and hence Australian) standard.
In EDI, an interchange is made up of one or more
messages (or
possibly functional groups containing messages of the
same type),
which in turn are composed of segments built up from one
or more
single or composite data elements.
[2] Nevertheless, Stallings & Van Slyke (and
others) only describe the US-centric ANSI X.12 standard...:-(
EDI Data Structures
An EDI message is the basic unit of transmission -
typically a
message can consist of an order, an invoice or a similar business
document.
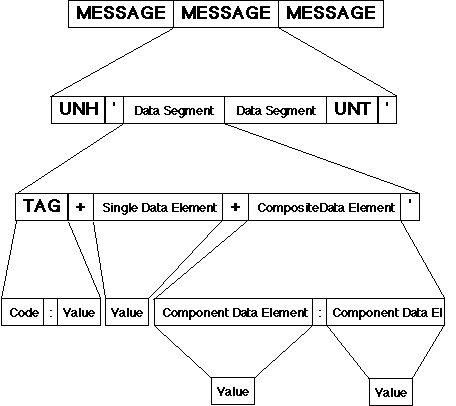
Original diagram from Standards Australia, AS 3801 - 1989
Typical EDIFACT Messages
Some EDIFACT message types:
- CREADV
- Credit Advice
- CREEXT
- Extended Credit Advice
- CUSDEC
- Customs Declaration
- DEBADV
- Debit Advice
- IFTMAN
- Arrival Notice
- IFTMBC
- Booking Confirmation
- IFTMBF
- Firm Booking
- IFTMFR
- International Forwarding & Transport Message
Framework
- INVOIC
- Invoice message
- ORDERS
- Purchase Order
- PAYORD
- Payment Order
- REMADV
- Remittance Advice
and many, many more ...
There are also a larger number of draft and proposed message types
awaiting standards approval. It is possible for a group of users
to suggest a new message type to meet an unusual business need.
EDI Implementation
There is a great deal of flexibility in the way EDI can be
implemented. Some approaches include:
- Use of a commercial EDI provider service, whereby users
establish a permanent or dial-in link to the provider who in turn
provides a "mail box" where messages are lodged to await delivery
to the recipient. The principle disadvantage of this occurs where
messages must be relayed to recipients connected to a different
EDI service.
- Use of a commercial electronic mail facility such as the OSI
X.400 service offered by Telstra - the advantage of this over
option 1. is that X.400 delivery is somewhat more universally
available.
- Delivery using the reliable transport service of the Internet
- either using the TCP protocol directly, or indirectly by
encapsulating EDI messages into SMTP electronic mail. This is the
obvious choice for future EDI users, the only lingering concerns
having to do with security.
EDI System Architecture
Key system entities include:
- Application Software
- is where the business information is
created
and used - eg: order entry and accounts payable systems.
- Translation Software
- is required to convert internal
representation of data to and from the standard formats used in
EDI. This can usually be supplied by the EDI provider as part of a
complete PC-based turnkey package.
Note: such PC-based translation software is regarded as suitable
for small businesses starting out with EDI. However:
- maximum gains from the technology are only attainable when the
EDI translation software is fully integrated with
corporate
databases such that information can flow between applications
without human intervention.
- This implies development (or purchase) of EDI translation
software on the corporate mainframe = big $$
EDI Security
Some concerns include:
- How can I be sure that my EDI traffic has reached the right
destination in a timely manner?
- How can I believe that the EDI messages I receive genuinely
come
from my trading partners?
- How can I be sure that my messages have not been corrupted in
transit?
- What would the impact on my business if a competitor could
read
my EDI traffic?
- What would be the impact on my business if my EDI service was
interrupted?
For X.400-based systems, security is built in, and may be
sufficient to meet the user's requirements. However, if it is
provided as part of the X.400 service instead of by the
end-users, there could be a cause for concern.
There is little inherent security in the Internet.
The EDIFACT group has addressed these concerns, and have
(apparently) released trial standards for security mechanisms
within the EDI specification itself.
Case Studies and the EDI Industry Group
Major Australian EDI users include:
- All of the motor vehicle manufacturers and most of their
component suppliers
- A large proportion of government departments, both state and
federal
and hundreds of others...
The Australian EDI industry body is the "EDI Council of
Australia", EDICA. Their brief also covers other
forms of
electronic messaging such as:
- Interpersonal (human–human) computer messaging, or electronic
mail and forms-based email.
- Human to computer messaging. Typical examples of this include
one-way email, or automatic computer generation and transmission
of FAX messages, called C-Fax by EDICA.
NB: EDICA also states "Many organisations, particularly those with
over $100 million in sales have already begun full scale trading
partner initiation programs. Very few have achieved successes
which they would consider to be commensurate with the time, effort
and money expended"
This lecture is also available in PostScript format.
The tutorial for this lecture is Tutorial #19.
Phil Scott

