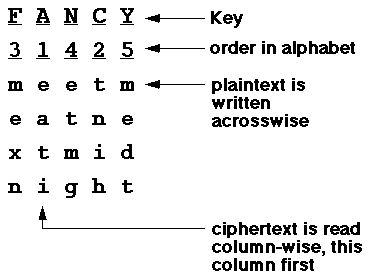
Hence, the ciphertext is:
Multi-stage transposition was the basis of the famous Enigma encryption machine used by German armed forces and famously cracked by the British intelligence service at Bletchely Park in the second world war.EATITNIHMEXNETMGMEDT
| Lecture 17: Introduction to Encryption | Copyright © 2005 P.Scott, La Trobe University Bendigo. |