previous |
start |
next
Authentication Example
A wishes to communicate with B. Each already has the other's public
key in their possession.
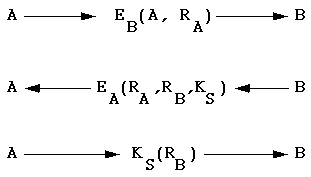
In the above, the R's are random numbers. Initially, A says "I am
A" and suggests a random number, the entire message being encrypted
with B's public key.
B responds with A's random number, a random number of her own, and
a suggested session key, all encrypted with A's public key.
Finally, A responds to B by encryping B's random number with B's
suggested secret key. Because no one else could have the
information to know KS, B is now confident that it is
talking to A.
previous |
start |
next