we also have:P = D ( E ( P ) )
This is true for RSA. Now consider Alice, who wishes to authenticate herself to a communications partner Bob. Bob already knows Alice's public key.P = E ( D ( P ) )
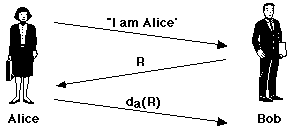
Alice announces to Bob that she wishes to communicate. Bob responds by choosing a large, single-use random number
R
(sometimes called a nonce) which he sends to
Alice. Alice encrypts the random number using her private
key, da and returns the
encrypted value to Bob. Bob applies Alice's public
key to the returned value, and if it decrypts to
R then he can be certain of the identity of his
communication partner. It's obvious that this protocol could be
extended to verify the identity of Bob as well. | Lecture 18: Encryption #2 -- Public Key Systems | Copyright © 2005 P.Scott, La Trobe University Bendigo. |