ipForwarding,
icmpInEchoes and
tcpMaxConn? Give solutions using each of the
get and get-next commands. Use a
command syntax of your choice, although the CMU SNMPlib syntax
given in the lecture notes would be
the most appropriate.
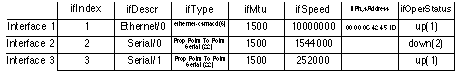
ifTable) in the interfaces portion of the
standard MIB, edited to fit the page. The table consists of a
sequence of ifEntry elements. Values shown are
from the router r-bgowan at Bendigo, which is
nowadays used as a backup (over ISDN) to the microwave link to
Bundoora.
- Describe interface 3 on this router.
- Draw the OBJECT IDENTIFIER subtree, in "tree" format, in
the region which defines the various
ifSpeedentries. You might find it helpful to refer to your lecture notes for some useful information here. - What would be the structure of an SNMP
get-requestto discover the speed, in bps, of interface 1. - What value would be returned by
get-next(...ifSpeed.2)?
{ system sysDescr }.
Of course, in the "Real World", we would normally
have to be more careful to ensure that the software we were using
was able to unambiguously fetch the variable we desired. How
should SNMP software resolve such abbreviations, especially with
numeric OBJECT IDENTIFIER strings? Hint: think of how Fully
Qualified Domain Names (FQDNs) are specified, compared to
abbreviated versions.