Network Monitoring
In most multiaccess networks, it is trivially easy for a host to set
its network interface into "promiscuous mode", and copy all data
frames which pass across the network.
This is called eavesdropping or (in some circles)
packet snarfing.
Once the host has copies of all the frames it desires, it can then
analyse them to discover the data they contain.
Most data transfers across the Internet are not encoded (or
encrypted) in any way Ð the data is simply sent as
plain text. Thus
it is simple to observe messages transmitted by others. This is the
origin of the (oft repeated, and generally true) assertion that
"The
Internet is insecure".
An area where this insecurity can present a serious
problem is
password authentication. At Bendigo, students can use the
TELNET
protocol to connect to the various Unix systems. The password which
is typed by the student is transmitted across the LAN as plain text,
and can be observed by any other student using freely available PC
software. You need to always be aware of this!
The solution is encryption - encoding the message so that
it is unintelligible to the intruder.
Encryption is a vast technical, scientific and political topic.
We will look briefly at a few aspects.
Cryptography Basics
A message to be encrypted (known as plaintext) is
transformed by the use of a function parameterised
by a key, thus:
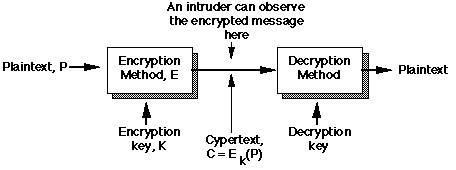
The security of the cyphertext depends on:
- The nature of the encryption method, or algorithm. It is nowadays
generally agreed that open publication of details of the
algorithm is a Good Thing.
- The secrecy of the key. Current opinion is that, given a
suitably powerful encryption algorithm, the security of the
system should depend entirely on:
- keeping the key secret and
- the length (usually measured in bits) of the key itself.
The Basic Algorithms
- Substitution Cyphers
- the simplest technique, whereby
each character in the message is replaced by another
using some rule. The order of the encrypted characters
is the same as in the plaintext. There are many examples
of this technique. Most fall into the general category of
monoalphabetic substitution, where the output
alphabet is the same as the input.
- Transposition Cyphers
- here the order of the
plaintext characters is changed, but the characters
themselves are not.
Simple implementations of both of these are (regardless
of key length) susceptible to various well known attacks,
and are not regarded as secure for any serious use.
The modern defence is to use basically the same ideas,
but with much more complex algorithms (see next slide).
Another approach (although rarely used) is the one-time pad,
(or Vernam Cypher) where a simple algorithm is used in
conjunction with a key of the same length as the message,
and employing a brand new key for every message transmitted
message. This is, in every respect, unbreakable, but rather
impractical for real-world use in most cases (although see
s/key).
DES - The Data Encryption Standard
DES is a block cypher, which operates on
64-bit data fragments, using a 56-bit key. The basic
DES algorithm is described as follows:
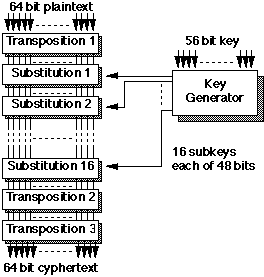
Note that DES is designed so that decryption is performed by
the exact same algorithm as encryption (using the same key -
hence single key), except performed in reverse.
The effectiveness of DES is based on the complexity of
the 19 stages. In the above diagram, two identical 64-bit
plaintexts will result in identical cyphertexts.
This is called the Electronic Code Book (ECB) mode
of operation.
DES In Practice
The ECB mode of operation is now rarely used, since it is
now generally agreed that it is breakable given sufficient
resources.
In the Chain Block Cypher (CBC) mode, each block
of plaintext is exclusive-ORed (XOR) with the cyphertext
output from the previous encryption operation. Thus,
the next block of cyphertext is a function of its
corresponding plaintext, the 56-bit key and the previous
block of cyphertext. Identical blocks of plaintext no
longer generate identical cyphertext, which makes this
system much more difficult to break.
The CBC mode of DES is the normal technique used for
encryption in modern business data communications.
A variation on CBC is used where the message may not be a
multiple of 64 bits, or where interactive (character at a
time) encryption and decryption is desired.
This is called Cypher Feedback Mode (CBM), and
uses shift registers to permit one byte at a time to be
encrypted or decrypted.
Public Key Systems
DES works well, but relies on both parties having a copy
of the same key. This can be a big problem.
In 1978, Rivest, Shamir and Adelman (RSA) developed a
solution called Public Key Cryptography. Details of
the underlying theory are outside the scope of this unit,
but the fundamental concepts are:
- A public key is used to encrypt and a separate,
different private key to decrypt the message.
- Each party involved generates a key pair.
- Each party publishes their public key.
- Each party secures their private key, which must remain secret.
- Assuming A desires to send a message to B, it first encrypts
the message using B's public key
- B can decrypt the message using its private key.
Since no one else knows B's private key, this is absolutely
secure - no one else can decrypt it.
- There still remain difficult problems of authentication
of public keys, compromised keys, bogus & out of date keys.
Further, Public Key encryption is very, very slow compared
to single key systems.
Other Encryption Applications
Authentication is the problem of proving that
someone you are communicating with is who you believe they are.
- This turns out to be one of the trickiest problems in
cryptography.
- Can be done if both parties share a common secret
key or keys, however...
- Diffie-Hellman key exchange protocol can be used
to establish shared secret keys but is complex and unwieldy.
- More usefully, trusted Key Distribution Centres
perform this function. See also Kerberos and Public
Key-based systems.
Digital Signatures are a form of authentication
applied to electronic documents.
- Single key and public key systems are known - both also
encrypt the message, which may be unneccessary.
- To authenticate without encryption, message digest functions
can be used. The most common is MD5 (previous version: MD4),
available on the Bendigo Unix systems. Message digests are
based on the idea that no two messages can ever generate the
same MD.
Clipper, Key Escrow and the Whole Political Thing
The USA and other governments are very interested in encryption.
Over the last few years, the USA has proposed several
variations of Clipper encryption systems.
- The original Clipper system was a hardware encryption
device based on the (secret) skipjack encryption
algorithm. It was originally intended to replace DES.
- Chip users (manufactuers?) register key with government:
key escrow. The key is split into two halves, which
are stored independently with different government agencies.
Current version: key recovery.
- Court-approved "wiretap" (ie, decryption)
operations require both halves of the key to access any data
transmissions. In addition, a released key can be coded so
that it only works for a limited time period.
Difficulties:
- Privacy concerns
- Commercial organisations are nervous about trusting
the government.
- some doubt about whether snooping decryption could be
avoided by clever users.
- Opinion: it won't fly.
If you are interested in further study of this area, have a look
at my incomplete list of cryptography
resources on the Web.
This lecture is also available in PostScript format.
The tutorial for this lecture is Tutorial #17.
[Previous Lecture]
[Lecture Index]
[Next Lecture]
Phil Scott


