http://amazon.com
and not http://hackers-r-us.com masquerading as them.
https://... Also, if you're using Netscape, the little
"key"or padlock icon will change. On the other hand, encryption is
computationallyheavy, so it's typically not used for normal Web pages.
WARNING: today's lecture contains far more information than you could reasonably be expected to digest--most of this content is not examinable!
X.509 defines a framework for authentication services -- usually as a repository of public key certificates. Such a certificate contains the public key of a user signed with the private key of a trusted certificate authority.
The standard does not specify a particular cryptographic algorithm, although an informative annex of the standard describes the RSA algorithm.
A certificate must, in general, be purchased from a trusted Certificate Authority. For some years, the only authority operating commercially was VeriSign Inc--in fact, early versions of Netscape would only accept certificates issued by VeriSign. There are now several (but still not very many) companies operating as certificate authorities. Commercial certificates cost in the range of several hundred $US per annum. It's also possible to purchase a private certificate, but takeup rates have been low.
This certificate is signed by the issuer to authenticate the binding between the subject (user's) name and the subject's public key. The major difference between versions 2 and 3 is the addition of the extensions field. This field grants more flexibility as it can convey additional information beyond just the key and name binding. Standard extensions include subject and issuer attributes, certification policy information, and key usage restrictions, among others.
Security: This is a secure document that uses a medium-grade encryption
key suited for U.S. export (RC4-40, 128 bit with 40 secret).
Certificate: This Certificate belongs to:
certs.netscape.com
Netscape Communications Corp.
501 E. Middlefield Rd., Mountain View, California, US
This Certificate was issued by:
Secure Server Certification Authority
RSA Data Security, Inc.
US
Serial Number: 0A:03:D9:06:5E:A5:E7:F0:F2:48:E2:EA:F4:7D:BC:CA
This Certificate is valid from Sun May 23, 1999 to Tue
May 23, 2000
Certificate Fingerprint:
83:B3:5D:50:73:21:C7:D9:E0:0D:AC:F1:42:31:68:B1
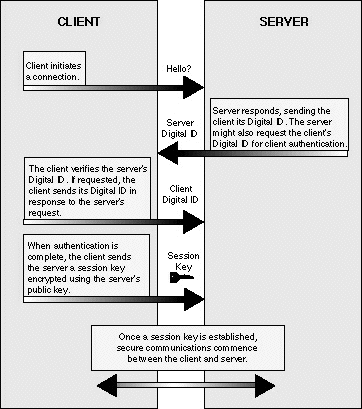
The basic idea of SSL is that it overlays the standard socket interface to TCP with a new socket library providing secure communications as required. Although it is the SSL standard that defines how the encryption is applied to Web transactions, the actual encryption itself is performed by a number of cipher algorithms. When an SSL browser and SSL server first communicate they mutually pick a cipher algorithm that both support. Some commonly used ciphers are listed in this table:
| Cipher | Bits | Description |
| 3DES | 168 | These are well-proven, 168-bit, triple-encryption ciphers. Not supported by products from Microsoft or Netscape. |
| IDEA | 128 | This cipher uses 128-bit keys but it is not commonly found in web browsers or servers. In the USA and Europe a license from Ascom AG is required to use these ciphers. |
| RC4 and RC2 | 128 | These ciphers use 128-bit keys, which normally offer a high degree of security. Inside the USA a license from RSA is required to use these ciphers. |
| Export RC4 and RC2 | 40 | These ciphers use 40-bit keys but are otherwise identical to their equivalent 128-bit versions. Servers and browsers produced by Netscape and Microsoft support these ciphers. Inside the USA a license from RSA is required to use these ciphers. |
 [Previous Lecture]
[Lecture Index]
[Next Lecture]
[Previous Lecture]
[Lecture Index]
[Next Lecture]