Subjects ->
Computer Networks ->
Lectures ->
Lecture #25
Lecture 25: The OSIRM in Brief, also Revision
Computer Networks Overview
This subject is composed of two halves[1]:
- The first half is a (roughly) "top-down" exposition of the layered
protocol components which make up the Internet.
- The second is a "grab bag" of various topics: network management,
encryption/security and technology of electronic commerce
In lecture #2, we saw a
layered network architecture model which provided the
conceptual framework for the first part of the subject.
We will briefly extend this model today by looking at the OSI
Reference Model (OSIRM).
[1] Actually, the split was closer to 2/3
for the first part and 1/3 for the second.
What is OSI?
...and why do I need to know about it?
- Because it's an important part of the history of computer networks.
It's also something you're likely to get asked about in job
interviews, which is where it really matters...
- It's a genuine International Standard (ISO/IEC IS 7498:1993) of
the International Organisation for Standardisation and
International Electrotechnical Committee(ISO/IEC)
- Mechanism: working draft --> committee draft -->
draft IS --> IS, with ballots at each stage.
- Was adopted (in part) as the definitive standard for network
architectures by most western governments: GOSIP
- National policy to mandate an OSI subset (or profile) for
government systems, discontinued in 1994/5.
- Huge and complicated, never fully implemented anywhere (see GOSIP,
as above) although some portions are commercially available.
- Has had some influence on the Internet community: some upper layer
OSI protocols (eg X.500, X.509, ASN.1) have been adopted in the
Internet.
The Classic OSI Reference Model Diagram
The Open Systems Interconnection Reference Model (OSIRM) specifies a 7
layer architecture for Computer Networking.
Diagramatically:
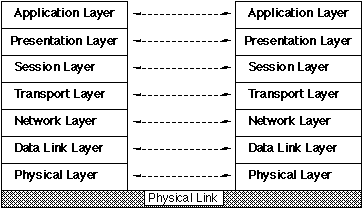
The conceptual intention here is that each the software which
implements each layer communicates with its Peer Layer
software, using services provided by the lower layers.
The software and protocols which implement a layer are called
entities in OSIRM.
The diagram is sometimes called (rather disrespectfully) the
7-layer-cake model.
OSI Layer Definitions
- Physical
- the actual "bit path" between two directly-connected
communicating "entities". Hardware.
- Data Link
- Framing and media access control protocols. It's quite useful
to have this separate layer.
- Network
- Equivalent to IP, the Internet Protocol. The OSI model
actually defined a very similar protocol to IP, called CLNS.
- Transport
- Pretty much exactly equivalent to the transport layer in the
Internet. The OSI protocol TP4 was functionally equivalent to
TCP.
- Session
- no real equivalent in the Internet architecture, this layer
was supposed to schedule connections, etc, subject to cost or
other constraints.
- Presentation
- the functions of this layer are integrated into the
application layer in the Internet. Mainly provides data
formatting services. ASN.1 was part of this layer.
- Application
- Very similar in function to the Internet application "layer",
although the OSI application protocols were, in general,
vastly more complex.
Why Did OSI Fail?
The development of OSI was a huge project, spanning
close to 20 years. Yet it failed, and the Internet is now dominant.
Why?
- Technically, the OSI protocols were often criticised for their
complexity and lack of "elegance". In fact, the protocols were
known to be quite difficult to implement. This alone is not a
sufficient reason.
- The TCP/IP protocol suite was supplied at no cost with BSD Unix,
the operating system of choice in academia and research throughout
the 1980s. By the end of the decade it was widely used.
- The OSI protocols suffered from a "specify first, implement later"
design philosophy. At a time when the designers were not really
sure of the best way to do things, this led to long delays before
any implementation could be undertaken. Classically, the same
problems have caused the failure of many large "Information
Systems", and for similar reasons.
- The Internet protocols were developed using an
"engineering" approach: "broad consensus and
running code". Implementation experience continually fed back into
design.
- etc...
The Exam Plan
- Question 1: Application Protocols
- This question is worth 30 marks (out of 120 total) and covers
material in
lecture 4,
lecture 5,
lecture 6,
lecture 7 and
lecture 8.
- Question 2: Network and Transport Protocols
- This question (and all subsequent) is worth 18 marks and covers
material in
lecture 3,
lecture 10 and
lecture 11.
- Question 3: Network Technologies
- Covers material in
lecture 12,
lecture 13 and
lecture 14. 18 marks.
- Question 4: Network Management
- Covers material in
lecture 15,
lecture 16 and
lecture 17. 18 marks.
- Question 5: Security
- Covers material in
lecture 18,
lecture 19 and
lecture 20. 18 marks.
- Question 6: Electronic Commerce
- Covers material in
lecture 21,
lecture 22,
lecture 23 and
lecture 24. 18 marks.
More Information
The following lectures are not explicitly examined:
Lecture 1: Computer Networks Overview
Lecture 2: A Network Architecture Example
Lecture 9: The Programming Interface
(all that sockets stuff, etc)
Lecture 25: The OSIRM in Brief, and Revision (ie, this
lecture)
- The exam is worth 60% of the final assessment for the subject.
- Note, also, that each question has many parts, and in some
cases, sub parts.
- Each of the parts/subparts is small, and carries between 2 and
6 marks. As usual, it's an exam which tests breadth of
knowledge more than depth. On the other hand, it's hard to
really stuff it up.
- It is in your interest to try and keep all the answers to each
question together in your answer booklet.
Please. If only for the sanity of the examiner...
- Revision:
- Old exam papers. Most important.
- Tutorial questions.
- Lecture notes.
If You Enjoyed It...
Finally, the advertising.
Computer Networks is, more than anything, an overview
subject. If you enjoyed this subject and you think you'd like to know
more, you should investigate the following LTU, Bendigo IT subjects:
- INT20DC:
Data Communications
-
- Offered in semester 2, taken by Phil Rice
- Covers the "bottom half" of the protocol stack in far more
detail.
- Overlaps slightly with Computer Networks.
- INT30WEN:
Web Engineering
-
- Offered in Semester 2, taken by yours truly, Phil Scott
- Extends the Computer Networks section on the Technology of Electronic
Commerce.
- Extensive programming required: you will learn all about
CGI programming in Perl and various related technologies.
- INT30ENS:
Encryption and Network Security
-
- Offered in Semester 2, taken by someone from the Department of
Mathematics (maybe Christopher Lenard?), and Phil Scott.
- Extends the Computer Networks sections on encryption and
security of Internet-connected computer systems.
Now the REAL advertising... This probably seems like
"just another subject" while you're at Uni, and it is. But the career
opportunities in this area are huge. Do not underestimate the value of
what you've learnt this semester -- it could be worth heaps to you!
There is no tutorial for this lecture. This is the last lecture.
 [Previous Lecture]
[Lecture Index]
[Next Lecture]
[Previous Lecture]
[Lecture Index]
[Next Lecture]
Copyright © 2001 by
Philip Scott,
La Trobe University.


 [Previous Lecture]
[Lecture Index]
[Next Lecture]
[Previous Lecture]
[Lecture Index]
[Next Lecture]