Subjects ->
Computer Networks ->
Lectures ->
Lecture #20
Lecture 20: Network Security
The Nature Of Attacks
Computer systems (hosts) connected to the Internet are subject to an
almost constant barrage of security attacks. Most attacks have at least
some of the following goals:
- To obtain unauthorised access to private, or secret, information
stored on the compromised system -- eg lists of credit card numbers
stored on commerce servers. Such access can be obtained by a wide
variety of means. This is probably the most important type of
attack.
- To use the compromised system as a start point for attacks on
other, more interesting, systems whilst "covering their tracks" --
the (so-called) Springboard Attack.
- Denial of service (DOS) attacks attempt to use up
system resources to inconvenience legitimate users. A classic
example is to send vast megabytes of (anonymous) electronic mail to
a target host in an attempt to exhaust its disk space. The
(relatively) recently developed Distributed Denial of
Service (DDOS) attacks are a particularly nasty form.
- A variation of the "unauthorised access" attack is where a Bad Guy
actually attempts to cause damage to the compromised system, for
example, by removing important files, changing configurations, etc.
Recent "Web site defacements" come under this category.
- etc, etc...
Internet Security
Most interest in security issues is in connecting to the Internet in a
secure way. Recall:
- An Internet-connected system uses the TCP/IP protocol suite. The
TCP/IP model of communications is based on server processes waiting
(at well-known ports) for remote sites to establish connections.
- A server process has very little information -- usually only an IP
address and a reverse DNS lookup -- about the identity of a remote
host which is attempting to connect. Even reverse lookups can be
compromised by manipulation of DNS tables or by IP
Spoofing, where a remote host generates IP packets that
look as though they came from some other system.
- Servers which generally accept all connections without any
(initial) security checks (such as
finger and
sendmail) can be vulnerable to various forms of
attack, such as attempted buffer over-running.[1]
- A major problem is the whether the sysadmin can
trust the server programs to be bug free...An
issue here is whether the vendor provides access to source code for
scrutiny.
[1]
A successful buffer overrun attack requires extremely detailed
knowledge of the vulnerable target system. However, many such exploits
have been observed over the years. The famous "Morris Internet Worm" of
1988 was based (among other things) on a buffer overrun attack on
sendmail, the Unix standard package for email delivery.
Firewall Security
A Firewall is usually implemented in the
organisation's "gateway" router, situated at the interface between the
Internet and an organisation's private network, thus:
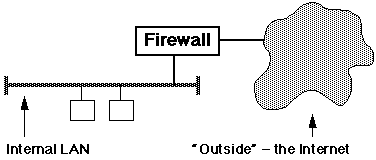
There are three classes of Firewall:
- Packet filtering firewalls
- Application gateways
- Circuit level gateways
Of these, the packet filtering type is the most common.
Because the firewall is simply an enhanced router (and
not a general-purpose computer system/host), it does
not itself run any vulnerable server processes.
Packet Filtering Firewalls
These only permit selected traffic to pass between
the "inside" and "outside" networks.
The decision to forward a packet or to discard it is made by looking
into its protocol headers, usually at either the IP source or
destination address. The TCP or UDP port numbers in the packet can also
be used.
TCP (and UDP) level filtering is more complex. and requires the
firewall router to keep much more "state" information. For example, a
particular site may allow outgoing TCP connections for
some services (ie, port numbers), but prohibit most
incoming TCP connections. This can be achieved by
examining the ACK bit in the TCP header: it is cleared in the first
connection request segment, and is set in all subsequent segments.
For example, the La Trobe University "gateway" router is configured to
block outgoing port 80 (HTTP) connections, thus forcing Web users
within the University to use the caching proxy server. At Nilai College, where this unit is
also offered, outgoing HTTP (port 80) connections are permitted and
most other services are blocked at the gateway router. Go figure
:-)
Packet Filtering Configuration
As an example of how access based on packet filtering can be
configured, consider the approach taken in Cisco(tm) routers.
An access list is used to define permisible packet flows through the
router. The general form of an access list entry is:
{ permit | deny } address [mask]
The entries have meaning thus:
permit | deny
- indicates whether this entry allows or blocks traffic from the
specified address.
address
- gives the source IP address.
mask
- this (optional) field is interpreted as a "bitmap" which
defines the significance of each bit in the preceding address
field. Every bit in the mask which has a "1" value indicates a
"don't care" bit in the address, whereas every "0" bit
indicates a bit in the address which must match exactly.
The access list for each interface can have many entries of the above
form.
In addition, an access list can be specified to restrict either
incoming or outgoing packets on the particular interface. Cisco's
Extended ACLs are used for transport-layer (and other
complex) filters.
More Complex Firewall Configurations
Most corporate firewall structures utilise a de-militarised
zone (DMZ, also called a "stub network") between the internal
LAN and the Internet, thus:
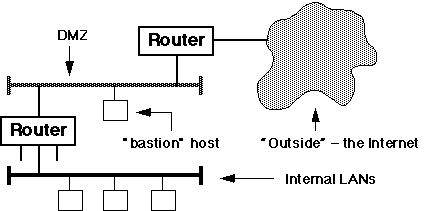
Both of the routers in this diagram are configured as packet filtering
firewalls. Note that the DMZ is, of necessity, a separate subnet.
Exercise: why?
There are many options for the level of filtering in the routers, and
for the functionality of the bastion host. These are examined in the
next slides.
Application Gateways
In this configuration, the only system which has access to the outside
Internet is the bastion host. In turn, the systems on the internal LAN
(nowadays often referred to as the "Intranet") can only establish TCP
connections to the bastion host, or gateway. Both of these conditions
are configured using TCP and IP address-based packet filtering in the
routers. No TCP connection (or even packet flow) is permitted between
the Intranet and the external Internet.
If users on the Intranet wish to use services provided on the
outside Internet (for example, to ssh, or "shell" into an external Unix
system) they must first connect to the gateway, and then use softare
running on it to access the exterior machine.
An example of such a structure is provided by an electronic mail
gateway which receives messages from the Internet. Typically, a mail
gateway in the DMZ receives messages addressed to an alias address,
such as:
P.Scott@latrobe.edu.au
and delivers (SMTP) the message to an appropriate second
(department-level) server within the Intranet. MX records in the DNS
support such mail gateway systems.
Circuit Level Gateways
These operate at the level of the TCP connection (or
circuit). In effect, the application gateway transfers
a copy of application-level data between the internal network and the
outside Internet instead of the IP packets themselves.
Such a structure might be used where an internal host wishes to, for
example, fetch a WWW page from a server in the external Internet. The
client web browser establishes a connection to a server which is
running on the gateway host. The gateway server in turn establishes a
second connection to the actual WWW server on the
external Internet, and passes the incoming HTML document back to the
internal browser process. Such a server (running on the gateway, or
bastion, host) is called a proxy.
One of the advantages of a proxy server is the caching
of external web pages, thereby potentially reducing traffic on the
connection to the outside Internet.
Real World Firewall Systems
Most installations combine both circuit level and application gateways,
using the DMZ model of the previous slides. As mentioned, this implies
the use of routers which can be configured to do packet filtering on
both IP addresses and TCP connections.
The bastion host normally runs, for example, the organisation's WWW
server, its FTP server (if applicable) and any other public information
services. It also usually acts as an email gateway. The WWW server
usually is configured as a proxy for the hosts
connected to the internal LANs (the Intranet). It may also perform a
similar function for other services such as FTP.
This type of structure can be very effective, combining many of the
best characteristics of all of the other types. However, the gateway
system must usually be a general-purpose timeshared (and therefore
Unix) system, which raises doubts about the safety and reliability of
the proxy software processes. This is not a solved problem, for obvious
reasons.
Although... Highly secure versions of Unix for just such applications
are now said to be available.
Other Issues
Important undiscussed (and firewall related) issues in network security
include:
- The importance of logging system activity in tracking break in
attempts, and the use of log files in subsequent court actions.
- Legal and ethical issues, both from the perspective of the system
manager and in relation to the crooks.
- Passwords -- their general applicability, the tendency of people
to share them around and the sacrosanct nature of
/etc/passwd
- Security within Unix (and other server environments), and
the use of tools such as
cops and crack.
- Network security analysis tools, including
nmap
and (earlier) satan.
- The entirely unresolved philosophical and ethical question as to
whether it is nobler to discuss issues like all of these in a full
and frank way, or to hide them and hope the students and other
potential bad guys don't hear about them... See, for example,
Charles Tomlinson's 1853 "Rudimentary Treatise on the Construction
of Locks" (available on lots of Web sites) for an excellent
viewpoint on this.
If you are interested, there are various Firewall-related sites on the Web with
much more information than can possibly be provided here.
The tutorial for this lecture is
Tutorial #20.
 [Previous Lecture]
[Lecture Index]
[Next Lecture]
[Previous Lecture]
[Lecture Index]
[Next Lecture]
Copyright © 2005 by
Philip Scott,
La Trobe University.




 [Previous Lecture]
[Lecture Index]
[Next Lecture]
[Previous Lecture]
[Lecture Index]
[Next Lecture]